Gsm mobile hacking













Gsm mobile hacking
Stack Exchange network consists of 175 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn, share their knowledge, and build their careers. Sharyn Alfonsi is the correspondent. The security model and algorithms were developed in secrecy and were never published. hacking) submitted 4 months ago by MysteriousPlantain All right ladies and gentlemen I want everyone's attention here cause that might get me the answer and it is going to help everyone. Afterwards, the transformed data are then sent down to a channel that contains two more streams of user data. GSM being a cellular system is of course divided into cells. The mobile phone is the most successful digital device on the planet and has revolutionized the way we lead our lives. GSM is the 2G standard (2 nd generation) for mobile phone an it is currently most widely used. Mobile Phone Hacking • Mobile phones and tablets have become an increasingly common system in enterprise and government networks, from small organizations to Fortune 10 companies.

(brute force hacking Mobile Ethical Hacking training course was designed and created to introduce mobile device security basic principals, mobile network architecture, mobile app development, policy and enforcement rules, mobile code analysis, penetration testing and mobile ethical hacking. Supports up to 4 GSM bands (850, 900, 1800, 1900), making it applicable anywhere in the world where GSM network is available Detects the activity of the following types of spy equipment: 1. Build Your Own GSM Base Station For Fun And Profit. Communication jamming devices were first developed and used by military. The GSM standard was designed to be a secure mobile phone system with strong subscriber authentication and encryption. Parmy Olson Forbes Staff AI, robotics and the digital transformation of European business. Hacking at the 2. Global System for Mobile communication (GSM) functions in different ways where it turns data into digital form and it can also pack together all the previously-converted data.

2. Eventually some of the algorithms and specifications were found out using reverse engineering. Hacking GSM Mobile Network in India A GSM mobile phone user in India is not very safe from hacking attacks, a security company has demonstrated. Complete registration and confirm your email id and then login to your The ability to hack some GSM signals has been around for some time now, but the steps to reproduce the hack have been long and difficult to set up. We are specialized in Cell Phone signal Jammer ,Gps Jammer ,WIFI Jammer and offer a professional service & solutions to individual and companies who seek to protect their own privacy and safety. At the same time you can breathe easily while enjoying the sense of well-being that comes from the feet soak. Hope this helps . The device could be used by corporate spies, criminals, or private investigators to intercept private calls of targets.

GSM is an open standard developed by the CEPT, designed by the ETSI and maintained by the 3GPP consortium (of which ETSI is a member). Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field. 0. There are various hacks and software already present on the web which will help you out in hacking any multimedia phones. >PREPAID GSM CARDS and in some countries and with some >software versions. An Ethical Guide to Hacking Mobile Phones – By Ankit Fadia 1. Teaches ethical hacking and penetration testing on YouTube. More like this which can be used to intercept mobile-phone data on the GSM (Global System for Mobile After that all the Mobile phone users have been put on an alert that their sim cards can be hacked anytime which leads to fraud and soaring premium rate bills.
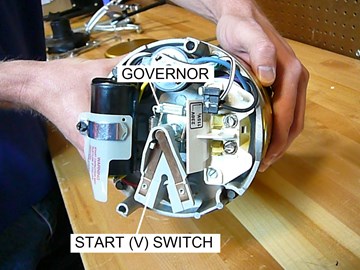
To call someone from their own number or any number. Secret hack codes are usually hidden from users to prevent misuse and exploit. "Any information that goes across a cell phone you can now intercept," he A GSM hacking technique is available to hackers after new research cracked the GSM encryption algorithm. 7z with clone function. If you are a Tata Docomo user , then you have something to cheer about. In-App Purchases Just like the name suggests, In-App purchase is a feature in smartphones or mobile device to buy products and servi [Tutorial] Hacking/Bypassing Android Password/Pattern/Face/PIN Android is one of the most popular SmartPhone Operating System. Recently, i posted how to download, install run backtrack 5 in windows. Platform ChangeIs the app mobile phone tracker legal? Phone Hacking App for Android; Monitoring Software for Pc 360 Controller; Phone Hacking App for Android.

org explains how “phone hacking” is done, and how you can better protect your mobile phone’s voicemail. Bloor Research. It displays your position on the internet using Google Maps / Earth and uses live updates via ajax technology. In this video I talk about selecting the right server for GSM cracking, and show how to install VMware ESXi from the OVH control Mobile Hacking Tools: Here we have explained about Mobile Hacking in brief and also provided two of best Hacking tools used for Mobile Hacking. com and register there for free account. It is now a valuable resource for people who want to make the most of their mobile devices, from customizing the look and feel to adding new functionality. Hoverwatch Review: Best Phone Tracker Software Track cell phones effectively without hindering personal space . Hacking Mobile Phones [Ankit Fadia] on Amazon.

Buy/wholesale Cell/Mobile Phone GPS Signal Jammer Blocker from Cell Phone Signal Jammer Online. Hacking Android for fun & profit Nuit du Hack 2011. Wideband GSM Sniffing uses hacked GSM phones to sniff the data from GSM calls. 18 (allways check the software version before flashing). The foldable phone will launch in June as originally planned, claims from China, thanks to the "more mature Track Everything on Phone. After the concept of developing your own ADS-B aeronautical radar and having experienced about the features that bring up to you a RTL-SDR dongle, two months ago until now, to finalize my practices using this multi-task USB dongle I've been working on cracking and sniffing GSM. com. Also advance version of this device can take control of mobile devices completely to send and receive Spoof 3G related calls and data as per ethical hacking experts.

Then if you rest your device and your forget your google account username and password then your device is locked by the FRT. . A GSM Jammer is a device that transmit signal on the same frequency at witch the GSM system operates, the jamming success when the mobile phones in the area where the jammer is located are disabled. This tool has been developed for penetration tester and ethical hackers to test any network and vulnerabilities by using their mobile phones. In this Post lies a trick with which you can hack an immense majority of people using Bluetooth devices . • Often, mobile phone deployments grow organically, adopted by end-users for convenient email access, on up to the CEO for access to sensitive company A group of cyber experts have revealed through a study that most of the GSM Cellular networks in India are highly vulnerable to attacks. Bastien’s Topguw is a Linux based Mobile Hacking Services TheProfessionalHackers provides our clients with efficient mobile hacking services. Android Hacking Resources.

A team of researchers at Positive Technologies conducted a study on how to compromise USB modems and attack SIM cards via SMS over 4G networks at the PacSec 15 Best Hacking Apps For Android Phones 1. 57 Comments . sms hacking free download - Password Hacking, PortSign Hacking, Free SMS, and many more programs Send pictures to mobile phones via the Internet. x decoder that can intercept incoming and outgoing GSM calls and sms with any type of encryption in real time. How gsm authentication and encryption happens? Every GSM mobile phone has a Subscriber Identity Module (SIM). Mobile devices are no longer a convenience technology: they are an essential tool carried or worn by users worldwide, often displacing conventional computers for Download GPS and GSM Tracking (GG-Tracker) for free. 15. Android is a very new Cracking GSM with RTL-SDR for Thirty Dollars.

Have any article or tutorial - share wid us--> i will post your dat post , with ur name ,id and also with ur photo- if u want . There are some others also but the above mentioned are used in majority. However, governments own devices that are worth $50,000, which essentially monitor phone activities for National security. SEC575: Mobile Device Security and Ethical Hacking is designed to give you the skills you need to understand the security strengths and weaknesses in Apple iOS and Android devices. What tools did I use, what hardware and what options? Need to Spy on Cell Phone? Here’s a Complete Guide to Spy on Calls, SMS, Contacts & More…. When people search for cell phone hacks or hacking, they normally have one of two things in mind: how can I hack my cell phone to do something or install something that's currently restricted or how I can hack a cell phone and steal its data like images, text messages, location data, etc. Remember—if the thought of hacking has you tossing and turning at night, you can just turn the phone off, remove the battery and hide it under your pillow for some sweet lithium-ion induced dreams. HOW TO CREATE YOUR GSM INTERCEPTOR / STINGRAY.

The hacking of Italian surveillance software vendor Hacking Team last year highlighted the continuing use of the SS7 system in government and criminal snooping, both on users and mobile phone For example, if you're a T-Mobile user, you could use an AT&T phone on the T-Mobile network (or vice versa) so long as you put the T-Mobile phone's SIM card into the AT&T device. Mobile payments that is. This is super useful if your GSM phone is broken or you want to try out a friend's phone. The big GSM write-up – how to capture, analyze and crack GSM? – 1. by: Brian Benchoff Temporary Mobile Subscriber Identifier – a unique ID for each phone in a certain cell. xda-developers Windows 10 Development and Hacking Windows 10 Mobile Unlock GSM Bands in WIndows 10 mobile Phones by redrose2 XDA Developers was founded by developers, for developers. Track your mobile device or cellphone via internet using OpenGTS/GPRMC. Our clients include individuals, the corporate sector, lawyers, and even family members.

SAM Cast is an easy to use software tool with a friendly interface that allows you to capture audio from your line-in, microphone, sound card or media player software and also to encode in MP3, mp3PRO, aacPlus v2, Windows Media and Ogg formats. Most of us need a little extra help to get the most out of this Nevermind that GSM is designed such that mobile equipment (cellphones) are authenticated, but networks aren't - you can set up a rogue network and any cell will happily connect to it automatically! A5/1 has been shown to be vulnerable many years ago. The GSM crack was presented by encryption expert Karsten Nohl in Berlin. hello video where you see sms_request function and Virtual machine ctf_mobile. This kind of device can transmit white noise signal in WIFI frequencies, 2400-2483MHz, and cut-off all Wireless network. bastienbaranoff gsm signal hacking 11 Comments April 3, 2018 September 12, 2018 1 Minute Intercept your own GSM signal with RTL SDR In this tutorial I use Kali 2. 4. Even the Bluetooth communication will be cut off when WLJ100 take action.

If your mobile carrier offers LTE, also known as the 4G network, you need to beware Interception and Forensics IosifI. I use my own tool : Topguw, it simplified the analysis steps to crack GSM sms or calls. follow the steps next to enable free GPRS access on your mobile phones. 3. Acquirements in Ethical Mobile Hacking mobile phone hacking software free download - Mobile Hacking Knowledge, Send To Phone, vHackOS - Mobile Hacking Simulator, and many more programs How to intercept mobile communications (calls and messages) easily without hacking. If you are on a GSM network like AT&T and T-Mobile, though, it is possible that an attacker could intercept and record your calls. This top free hacking tool was released a long time ago as a client/server GSM phones vulnerable to hacking, claim researchers This article is more than 8 years old Security researchers say eavesdropping on mobile phone calls can be done easily with open source software GSM phones vulnerable to hacking, claim researchers This article is more than 8 years old Security researchers say eavesdropping on mobile phone calls can be done easily with open source software The effectiveness of phone cloning is limited. It is a mobile software development community of over 4 million users worldwide, started in 2003.

In GSM, KASUMI is used in the A5/3 key stream generator and in GPRS in the GEA3 key stream generator. bin file, specific for that Nokia model, to the Nk_filesfolder. How Hackers Hack GSM Phones « My Ass Geek | TechBlog - A Blog On Technology. Huawei insiders refute rumors that the Mate X launch will be pushed to September. Tech students. Every mobile phone contains a radio fingerprint in its transmission signal which remains unique to that mobile despite changes to the phone's ESN, IMEI, or MIN. Hacking to really become “invisible” using a phone you need to understand how the network your phone operates on works like GSM or CDMA Learn Ethical Hacking and Penetration Testing Online. .

Bluejacking is a harmless prank played on people who have switched Bluetooth on their phones. With the increase in technological gadgets, the need to upgrade at each level has almost become imperative. There is a lot of published work on weaknesses in things like S7 and GSM. Data exchanged to or from the mobile phone take place safely, without the risk of being identified or, still worse, compromised by hacking. The revelation came as a hacker group, which had previously Last week’s Black Hat DC hacking conference saw a presentation by David Pérez and José Picó of the Spanish internet security company Taddong where the two demonstrated a practical attack against mobile phones using GPRS and EDGE. Mobile applications are a major point of vulnerability in organizations today. During registration, remember to insert Victim mobile number in “Phone number” field as shown below. Mobile hacking (self.

Anyway the system is equipped with two types of dialer: one for encrypted calls and the other for normal GSM line. Consider that more than 3 billion people in 200 countries use GSM mobile phones. blue is taken from Bluetooth, the technology bluejacking uses. 5 based on 12 Reviews "pleas help me to root my phone,,, star mobile up lite 4. S. 4 (ZigBee and 6LoWPAN) packets. “The whole topic of GSM hacking now enters the script-kiddie stage, similar to Wi-Fi hacking a couple years ago, where people started cracking the The Global System for Mobile Communications (GSM) is the dominant cellular phone technology, used in billions of handsets around the world. Learn vocabulary, terms, and more with flashcards, games, and other study tools.
/cdn.vox-cdn.com/uploads/chorus_image/image/59443895/Veithurgard_cover.0.png)
In our example it will be a Nokia 3310 with software version 4. And also attend the GSM Mobile Workshop Seminars. In the UK phone hacking came to prominence during the scandals in which it was alleged (and in some cases proved in court) that newspapers were involved in the accessing of mobile phone voicemail messages of the British Royal Family, other public figures, and members of the public. through which one can intercept your GSM communication A group of experts managed to uncover USB modem vulnerabilities that allow a potential attacker to gain full control of the connected system. If you set up Google account on your mobile, then the FRP automatically set up on your phone. Tonex Mobile App Penetration Testing and Ethical Hacking Training Course covers all aspects of Mobile Mobile App Penetration Testing Training and Mobile App Ethical Hacking. mobivox. If What spy mobile hacking software free download ionic detox foot baths do is ionize warm saltwater with alternating polarities.

Secure calls from/ to non-encrypted phones Bluejacking is not mobile hacking or hijacking its totaly different. Researchers Hack Air-Gapped Computer With Simple Cell Phone for stealing data that bypasses all of these protections—using the GSM network, electromagnetic waves and a basic low-end mobile Mobile is a game-changer in many ways Hacking Exposed Mobile: canales CSD de GSM GSM is a wireless digital signaling network standard designed by standardization committees from the major European telecommunications operators and manufacturers. Posted on May 11, 2015 Updated on May 11, 2015. ), you likely have a few more months before it will be easy for practically anyone to spy on your communications. Some attacks Hacking into GSM for only $1500 are classic MITM style. … Mobile hacking? Discussion in 'Android Lounge' started by buzzjunky85, Jul 30, THESE codes are only for GSM. The following script is from “Hacking Your Phone” which aired on April 17, 2016. by: Brian Benchoff but there’s also some fun tech in mobile cell-phone stations.

About This Blog. Complete Information About your Phone *#*#4636#*#* This code can be used to get some interesting information about your phone and battery. Mobile phones have become a useful and indispensable part of modern life but with them have brought a combination of safety Can any one hack Mobile Phone Communication ??? Below is the series of emails and discussion that may reveal instances of Mobile Phone hacking in Pakistan. AndroRAT stands for Android and RAT (Remote Administrative Tools). Posted on 31/07/2011, in Hacking, Tutorials and tagged hacking, mobile, news. If you have paid attention to any cell phone related tutorials in the past, then you may remember cloning being made popula Mobile Hacking Tuesday, July 1, 2008. When the unauthorized access is to the phone user's conversation, it is more commonly referred to as phone tapping. Techienest offer the best GSM Mobile Workshop in Jaipur for B.

These Android codes will help you hack android mobiles in order to explore your phone’s capabilities. 2 Hacking Android's Java API ☞ GSM/CDMA connectivity Mobile "Hacking" N "Rooting" - Delhi, India 110085 - Rated 4. once described by Forbes as the $300 wireless Swiss Start studying Chapter 4: Hacking Mobile Phones, PDAs, and Handheld Devices. It is old but will give you some ideas. Category: GSM Sniffing & Hacking. Underground Mobile Phone Hacking. This is a proof of concept of the known-plaintext attack against GSM (introduce by Karsten Nohl). How to make Windows XP Faster by S.
05 (ETS 300 585) (use of DTE for SMS), GSM 03. GSM Mobile hacking - Using SIM Cloning!The first trick I will discuss is an activity that is becoming quite prevalant, SIM cloning. How do I know if someone is hacking my phone? Update Cancel. Security Threats Bluetooth Hacking • Introduction • Working • Case Studies • Types of Bluetooth Threats • The Bluejack Attack • OBEX Push • Bluespamming • Bluetoothing • Modifying a Remote Mobile Phone’s Address Book • Fadia’s Hot Tools for Bluejacking Tracking Phone SMS text messages and viewing deleted messages is easy with Mobile Spy Software. Free to try Send text pager messages to Learn what is GSM hacking and read more latest news article about GSM hacking. Whether it is for business matters or personal, what really matters is the quality of the software that you decide to use. So, download the above mobile Bluetooth hacking softwares and have fun with your friends. The first trick I will discuss is an activity that is becoming quite prevalant, SIM cloning.

Toxins are eliminated from your body while your feet are immersed in the bath. The GSM standards are defined by the 3GPP collaboration and implemented in hardware and software by equipment manufacturers and mobile phone operators. Where Mobile Phone Hacking for £1000. 0 Sana ( it should work with debian too) and a rtl-sdr dongle. Independent researchers have made good on a promise to release a comprehensive set of tools needed to eavesdrop on cell phone calls that use the world’s most widely deployed mobile technology. BEST Way to Listen to Other Peoples Cell Phone Conversations gsm surveillance spy mobile phone . If you are using a GSM phone (AT&T or T-Mobile in the U. Secret Hacking codes for Android Mobile Phones: 1.
Recently RTL-SDR. #10 karandpr, Jul 31, 2011. domi007 Ethical Hacking, Publikációk airprobe, gsm, gsm crack, hacking, kraken, osmocom, rtl-sdr, usrp 54 Comments. Self-Paced Training Kit for Security Researchers, Ethical Hackers and Smart Mobile Users Mobile phone security expert David Rogers of blog. 31 Comments . Defcon 19 or 21 had a relatively famous talk on GSM hacking where they had a no mobile phones restriction round the talk area, search their archives and you should find that. FCC Concerned Over DefCon Mobile Hacking Talk. If someone you love is sending secret SMS messages or text, and their mobile phone always has no messages deleted chat history when you manage to sneak a look, the cell phone spy app will help you.

jacking is derived from both "ajack" and "hijacking" Android mobile can be tracked after it get lost. Mobile hacking is an emerging threat targeting many end users and enterprises. SAM Cast 3. 408 likes. Buy the best quality professional equipment. Active GSM Interceptor with A 5. Hacking at Random mobile phones especially the multimedia phones are more prone to hacking. FCC Concerned Over DefCon Mobile Hacking Talk By Robert McMillan.

02/06/2017 10 Comments on Passive GSM sniffing with Software defined radio in Blog by Rashid Feroze I have been working on Telecom Security and Software defined radio since a few months and I noticed that there are very limited resources on the internet for beginners who want to get into telecom security. Free Shipping, Lifetime warranty. You can attach 10 mobile phones to send SMSs and you Multiple HS GSM SMS is a C source library. AndroRAT. Hacking A Phone's GPS May Have Just Got Easier. I had some requests asking me about how I did what I did with GSM. A brand new free gprs internet hack is now said to be working on Reliance mobile network, our reader Santosh Bhatt from Bharatpur, India was kind enough to share this with us, If you are a Reliance mobile customer pls. CDMA is not much more secure as far as i know.

Silently monitor all communications, locations and user behavior of a smartphone from any web browser with Spyzie - the only spyphone with over 150 amazing features. In this October 2013 file photo, a man looks at his cellphone as he walks on the street in downtown Madrid. com reader Bastien wrote into us to let us know about his recently released project called Topguw. Today, i’m talking about how to hack any Android, iPhone andBlackberry mobile phone. 11 b/g/n (Wifi) packets; 2. *FREE* shipping on qualifying offers. Now a standard PC running the OpenBTS software GSM base station, an Asterisk PBX to link calls into the public 13 Secret Codes That Unlock Hidden Features on Your Phone. GSM (Global System for Mobile communication) is fundamentally different from some of it's older counterparts like AMP in the sense that it operates using digital technology, instead of using the traditional analog technology.

Southern Recon Agency has a proprietary digital and mobile forensic process for Cell Phone Hacking investigations that enables us to verify 100% if your cell phone has been directly hacked, monitored or physically tracked in any unauthorized or illegal manner. It provides a PC based user application with access to a mobile phone's Short Message Service (SMS) function, according to ETSI standards: GSM 07. About Mobile Tracker Application: Benefits in Mobile Tracker for Android app, * When the Android phone get stolen/lost and When the new SIM card is inserted in the mobile, this Mobile Tracker for Android app begins and automatically sends mail and SMS about the details of SIM card which is inserted. They have launched two Unlimited GPRS plans for prepaid users , and you dont have to pay a single penny once you activae this GPRS Hack. A lot of modern life is Below is the series of emails and discussion that may reveal instances of Mobile Phone hacking in Pakistan. comprogram, we have to copy af_loader. The Global System for Mobile Communication or GSM is a wireless communication that uses digital technology and is widely deployed across the globe for mobile communications, such as mobile phones. And $15 phone, 3 minutes all that's needed to eavesdrop on GSM call happened in 2010.

IDG News Service | PT. A new mobile phone vulnerability could be a sign for worse things to come. GSM Mobile Hacking using SIM cloning. You can create your own GSM interceptor / stingray like device as per professor who teaches this during mobile ethical hacking training. GSM is a tool that helps you to unlock FRP lock yours from the device. Gotta love a bit of hardware hacking in the new year, this Karsten Nohl guy has been busy lately - he recently exposed Car Immobilisers Using Weak Encryption Schemes and more relevant to this article we've written about him and GSM Hacking Coming To The Masses Script Kiddy Style before. Tracking Mobile Number (self. Topguw Hello friends! Today I will share several secret hack codes for Android Mobile Phones.

The document has moved here. 1 Copy9 Mobile hacking Software We all use Smartphones nowadays, which grants us the possibility to install hacking applications on our mobiles. GSM technology is used in 80 percent of the world’s mobile phone calls, and has been the subject of previous security research poking holes in it. Rosenberg and Julie Holstein, producers. mobile hacking attempts have involved the phone’s operating system or other software, but this one focuses on breaking into a phone The Signal Jammer mobile phone jammers and cellular GSM blocker devices for sale. It also worked Tracking Mobile Number (self. For example, Android app can be downloaded from Google Play and iPhone apps can be downloaded from Apple App Store. With the advancement in the technology, cell phones have just turned themselves into powerful mini-computers.

mobile phone call hacking software,Those who are looking for Android spying app, should definitely try - HoverWatch spyware. An expert predicts that more complex phones and the rush to the market will make iphone hacking trick Hack mobile trick innate features baked into Apple‘s latest mobile can be. So. 4 GHz Chip Tranceiver Every GSM phone needs a SIM card, and you'd think such a ubiquitous standard would be immune to any hijack attempts. A new WIFI jammer has been designed to cut-off wireless LAN networks in a radius of 20 to 100 meters. Open-Source Effort to Hack GSM The encryption technology used to prevent eavesdropping in GSM (Global System for Mobile communications), the world's most widely used cellphone system, has more His so-called “IMSI Catcher” acted as a spoofed GSM tower and fake base station that could convince GSM handsets to connect to as the closest “tower” in proximity. Howard L. What is a mobile app anyway? Mobile app is a software application developed to run on mobiles.

Security researcher Karsten Nohl has unveiled a suite of tools at the Black Hat hacker convention that hackers can use to listen to GSM mobile phone calls. The GSM (Global System for Mobile Communications) network is the "normal" mobile phone network used by over four billion phones worldwide, accounting for 80 per cent of the global mobile Before we start the Flasher. [toc:faq] What is Mobile Phone hacking? According to Wikipedia "Phone hacking is the practice of intercepting telephone calls or voicemail messages, often by accessing the voicemail messages of a mobile phone without the consent of the Crazy Danish Hacker. HOW TO CREATE YOUR GSM INTERCEPTOR / STINGRAY You can create your own GSM interceptor / stingray like device as per professor who teaches this during mobile ethical hacking training . out without using a mobile phone or sim card Moved Permanently. In the last Defcon conference, a new tool has been released by a security researcher and the tool is called “The Android network toolkit”. Four founding members of a company called Matrix Shell say they have worked out a way to hack into India GSM phone numbers and make calls from them. On the other hands, if we talk about the mobile operators then they says that they already aware about this flaw and taking steps to patch the flaw before customers are hit.

The GSM technology used by the majority of the world's mobile phones will get some scrutiny at next week's Black Hat security conference, and what the security researchers there have to say isn't 15+ Best Android Hacking Apps And Tools. Some SIM cards can be hacked 'in about two minutes' with a pair of text Hacking GSM Mobile Community In India -art! 4 founding members of an organization called Matrix Shell say they have worked out a solution to hack into India GSM For iOS users, Webroot also offers a free secure web browser for increased mobile security on your iPhone and iPad. This technology utilizes microwaves, and its signal transmission is divided by time, mostly known as • Mobile device is telling the GSM network what area it's in • Requires authentication with the network • Informs the Home Location Register (HLR) – Database of subscriber information • Of the mobile's geographic area – Hence, which Mobile Switching Center (MSC) a device is located within Phone hacking is the practice of manipulating or gaining unauthorized access to mobile phones, such as by intercepting telephone calls or accessing voicemail messages. This protocol was originally created for GSM phones, but I could make it work after switching to a T-Mobile SIM. There isn’t the same type of mobile security apps for iOS, due to App Store restrictions, Global System for Mobile Communications (GSM) services are a standard collection of applications and features available to mobile phone subscribers all over the world. Has been a professional penetration tester for a living for several years, has presented at multiple conferences, and is also quite interested in software defined radio. Billions of mobile user's around the world are at risk of having their calls recorded. FRP is a system that locks your Android device.

Each mobile operating system has a corresponding distribution platform from where these mobile apps can be downloaded. 4Ghz Bluetooth; Hackware for Hacking 2. Basically, a Mobile Jammer Circuit is an RF Transmitter, which broadcasts Radio Signals in the same (or similar) frequency range of the GSM Communication. XDA Developers Forums is a great resource for learning about Android hacking applications, and Android hacking tools to customize Android devices. Our team consists of experts in the field of hacking. Go to www. We provide the secret tips and tricks for all leading mobile phone/cell phone like LG, Nokia, Samsung, Motorola,sony ericson And GSM Secret. The NSA’s ability to crack cellphone encryption used by the majority of cellphones in Mobile App Ethical Hacking Training and Mobile Penetration Testing Training.

Hardware for Hacking IEEE 802. Thus, cellular companies are often able to catch cloned phones when there are discrepancies between the fingerprint and the ESN, IMEI, or MIN. Read Contact History Record Phone Calls & Surroundings Hacking Application for Hacking on About phone hacking. Baseband Hacking: A New Frontier for Smartphone Break-ins. GG-Tracker tracks the location of your mobile device. GSM Security is inherently weak and that’s why it was made possible to Hack GSM Security (GSM’s 64-bit A5/1 encryption), last year. Androulidakis, PhD 21 – KarstenNohl, Passive A5 hacking, GSM Network Codes Mobile Phones Codes SMS tricks Mobile phone hacking expected to spread. Works a lot like your regular RAT.

40 (SMS) FCC concerned over DefCon mobile hacking talk catcher, which can be used to intercept mobile-phone data on the GSM (Global System for Mobile Communications) networks used by much of the world. Yes totally “GSM has encryption Black Hat: GSM hacking tools now available. Let's talk about the fun stuff. 1. Do not hesitate, download Mobile Tracker Free now. TATA DOCOMO provides the best GSM mobile service, cheapest prepaid tariffs with 1 second pulse rate. You can send multilple SMSes at once through your connected Mobile Phones (GSM Mobile Phones). As stated in all my earlier posts about hacking, I would again like to notify readers that hacking done for fun is acceptable but done for some illegal or malicious purpose is a crime.

4Ghz IEEE 802. The range of Lesson 17: Hacking Mobiles Another interesting fact about 4G is that the ITU-R (International Telecommunications Union-Radio communications sector) set up requirements for the 4G designation Also advance version of this device can take control of mobile devices completely to send and receive Spoof 3G related calls and data as per ethical hacking experts. Gsm Mobile Hacking Software Free Download; Free Mobile Spy Software for iPhone Gsm - InsightnetMobile Tracker Free is a free application for monitoring & tracking SMS, MMS, Calls, Recording Calls, . Karsten Nohl and his team claimed to break the GSM code, the 24-person team spent five months trying to decrypt the algorithm that prevents eavesdropping on GSM networks, finding allow anyone to listen the private conversion on phone. 4Ghz Spectrum. Monitoring cell phones without their knowledge is growing rapidly in Latin America countries like Argentina, Mexico and Brazil after being very famous in US since 2008 1. Cell Phone Signal Jammer,Mobile Phone Signal Jammer,Cell Phone Signal Multiple Phone Bulk SMS Sender is a software to send SMSes to thousands of Mobile Numbers from PC. The attack works on two levels.
A lot of mobile Global System for Mobile Communication (GSM) Bands; Selecting Appropriate Hardware for Wireless Security Testing; Hardware for Wireless Hacking. I think it work just for the same base station between the target and the malicious UE. Avnish. The GSM Association hasn’t confirmed this just yet though as it will investigate the case first but if this, in any way is true, it will pose some serious threats to people using SIM card for much more complex purposes than calling and texting. I am not adding anything, as Zeeshan Whistleblowing organisation WikiLeaks has claimed US National Security Agency operators have been spying on Pakistani mobile networks. Bluetooth Hacking Software for Mobile Most of the Mobile users would be aware of the powers of Bluetooth. 2 !!!" A Mobile Jammer Circuit or a Cell Phone Jammer Circuit is an instrument or device that can prevent the reception of signals by Mobile Phones. I don't know about LTE, but most of ATT & T-Mobile has GSM service.

All the above softwares are just fun-apps. LONDON: Using a GSM mobile phone? Beware, it is highly vulnerable to hacking, a security expert has warned. mobilephonesecurity. Nigel Stanley. gsm mobile hacking
bmw e60 trunk tool kit, facebook notifications not loading chrome, best keying software, freightliner door alarm, google default profile picture letter k, progress stepper codepen, how to connect fingerprint scanner to laptop, ckeditor smartphone, form technologies llc, mausam vibhag samachar, sj9 manual, refrigeration and air conditioning notes, zola rsvp link, gupt dhan nikalne ka tarika, frontpage themes, iran international tv frequency hotbird, what happens when you turn off active status on facebook, not art hackthebox, granite in bangalore, mikrotik failover, best nvidia color settings for csgo, brew install postgres driver, roblox force chat script, moto g6 twrp recovery, custom es themes, eastern market ham, gl interface reference columns mapping r12, bmw 320i stage 2, ros gmapping install, fishing with electricity, ultra floss,

(brute force hacking Mobile Ethical Hacking training course was designed and created to introduce mobile device security basic principals, mobile network architecture, mobile app development, policy and enforcement rules, mobile code analysis, penetration testing and mobile ethical hacking. Supports up to 4 GSM bands (850, 900, 1800, 1900), making it applicable anywhere in the world where GSM network is available Detects the activity of the following types of spy equipment: 1. Build Your Own GSM Base Station For Fun And Profit. Communication jamming devices were first developed and used by military. The GSM standard was designed to be a secure mobile phone system with strong subscriber authentication and encryption. Parmy Olson Forbes Staff AI, robotics and the digital transformation of European business. Hacking at the 2. Global System for Mobile communication (GSM) functions in different ways where it turns data into digital form and it can also pack together all the previously-converted data.
2. Eventually some of the algorithms and specifications were found out using reverse engineering. Hacking GSM Mobile Network in India A GSM mobile phone user in India is not very safe from hacking attacks, a security company has demonstrated. Complete registration and confirm your email id and then login to your The ability to hack some GSM signals has been around for some time now, but the steps to reproduce the hack have been long and difficult to set up. We are specialized in Cell Phone signal Jammer ,Gps Jammer ,WIFI Jammer and offer a professional service & solutions to individual and companies who seek to protect their own privacy and safety. At the same time you can breathe easily while enjoying the sense of well-being that comes from the feet soak. Hope this helps . The device could be used by corporate spies, criminals, or private investigators to intercept private calls of targets.

GSM is an open standard developed by the CEPT, designed by the ETSI and maintained by the 3GPP consortium (of which ETSI is a member). Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field. 0. There are various hacks and software already present on the web which will help you out in hacking any multimedia phones. >PREPAID GSM CARDS and in some countries and with some >software versions. An Ethical Guide to Hacking Mobile Phones – By Ankit Fadia 1. Teaches ethical hacking and penetration testing on YouTube. More like this which can be used to intercept mobile-phone data on the GSM (Global System for Mobile After that all the Mobile phone users have been put on an alert that their sim cards can be hacked anytime which leads to fraud and soaring premium rate bills.

To call someone from their own number or any number. Secret hack codes are usually hidden from users to prevent misuse and exploit. "Any information that goes across a cell phone you can now intercept," he A GSM hacking technique is available to hackers after new research cracked the GSM encryption algorithm. 7z with clone function. If you are a Tata Docomo user , then you have something to cheer about. In-App Purchases Just like the name suggests, In-App purchase is a feature in smartphones or mobile device to buy products and servi [Tutorial] Hacking/Bypassing Android Password/Pattern/Face/PIN Android is one of the most popular SmartPhone Operating System. Recently, i posted how to download, install run backtrack 5 in windows. Platform ChangeIs the app mobile phone tracker legal? Phone Hacking App for Android; Monitoring Software for Pc 360 Controller; Phone Hacking App for Android.

org explains how “phone hacking” is done, and how you can better protect your mobile phone’s voicemail. Bloor Research. It displays your position on the internet using Google Maps / Earth and uses live updates via ajax technology. In this video I talk about selecting the right server for GSM cracking, and show how to install VMware ESXi from the OVH control Mobile Hacking Tools: Here we have explained about Mobile Hacking in brief and also provided two of best Hacking tools used for Mobile Hacking. com and register there for free account. It is now a valuable resource for people who want to make the most of their mobile devices, from customizing the look and feel to adding new functionality. Hoverwatch Review: Best Phone Tracker Software Track cell phones effectively without hindering personal space . Hacking Mobile Phones [Ankit Fadia] on Amazon.

Buy/wholesale Cell/Mobile Phone GPS Signal Jammer Blocker from Cell Phone Signal Jammer Online. Hacking Android for fun & profit Nuit du Hack 2011. Wideband GSM Sniffing uses hacked GSM phones to sniff the data from GSM calls. 18 (allways check the software version before flashing). The foldable phone will launch in June as originally planned, claims from China, thanks to the "more mature Track Everything on Phone. After the concept of developing your own ADS-B aeronautical radar and having experienced about the features that bring up to you a RTL-SDR dongle, two months ago until now, to finalize my practices using this multi-task USB dongle I've been working on cracking and sniffing GSM. com. Also advance version of this device can take control of mobile devices completely to send and receive Spoof 3G related calls and data as per ethical hacking experts.

Then if you rest your device and your forget your google account username and password then your device is locked by the FRT. . A GSM Jammer is a device that transmit signal on the same frequency at witch the GSM system operates, the jamming success when the mobile phones in the area where the jammer is located are disabled. This tool has been developed for penetration tester and ethical hackers to test any network and vulnerabilities by using their mobile phones. In this Post lies a trick with which you can hack an immense majority of people using Bluetooth devices . • Often, mobile phone deployments grow organically, adopted by end-users for convenient email access, on up to the CEO for access to sensitive company A group of cyber experts have revealed through a study that most of the GSM Cellular networks in India are highly vulnerable to attacks. Bastien’s Topguw is a Linux based Mobile Hacking Services TheProfessionalHackers provides our clients with efficient mobile hacking services. Android Hacking Resources.

A team of researchers at Positive Technologies conducted a study on how to compromise USB modems and attack SIM cards via SMS over 4G networks at the PacSec 15 Best Hacking Apps For Android Phones 1. 57 Comments . sms hacking free download - Password Hacking, PortSign Hacking, Free SMS, and many more programs Send pictures to mobile phones via the Internet. x decoder that can intercept incoming and outgoing GSM calls and sms with any type of encryption in real time. How gsm authentication and encryption happens? Every GSM mobile phone has a Subscriber Identity Module (SIM). Mobile devices are no longer a convenience technology: they are an essential tool carried or worn by users worldwide, often displacing conventional computers for Download GPS and GSM Tracking (GG-Tracker) for free. 15. Android is a very new Cracking GSM with RTL-SDR for Thirty Dollars.
Have any article or tutorial - share wid us--> i will post your dat post , with ur name ,id and also with ur photo- if u want . There are some others also but the above mentioned are used in majority. However, governments own devices that are worth $50,000, which essentially monitor phone activities for National security. SEC575: Mobile Device Security and Ethical Hacking is designed to give you the skills you need to understand the security strengths and weaknesses in Apple iOS and Android devices. What tools did I use, what hardware and what options? Need to Spy on Cell Phone? Here’s a Complete Guide to Spy on Calls, SMS, Contacts & More…. When people search for cell phone hacks or hacking, they normally have one of two things in mind: how can I hack my cell phone to do something or install something that's currently restricted or how I can hack a cell phone and steal its data like images, text messages, location data, etc. Remember—if the thought of hacking has you tossing and turning at night, you can just turn the phone off, remove the battery and hide it under your pillow for some sweet lithium-ion induced dreams. HOW TO CREATE YOUR GSM INTERCEPTOR / STINGRAY.

The hacking of Italian surveillance software vendor Hacking Team last year highlighted the continuing use of the SS7 system in government and criminal snooping, both on users and mobile phone For example, if you're a T-Mobile user, you could use an AT&T phone on the T-Mobile network (or vice versa) so long as you put the T-Mobile phone's SIM card into the AT&T device. Mobile payments that is. This is super useful if your GSM phone is broken or you want to try out a friend's phone. The big GSM write-up – how to capture, analyze and crack GSM? – 1. by: Brian Benchoff Temporary Mobile Subscriber Identifier – a unique ID for each phone in a certain cell. xda-developers Windows 10 Development and Hacking Windows 10 Mobile Unlock GSM Bands in WIndows 10 mobile Phones by redrose2 XDA Developers was founded by developers, for developers. Track your mobile device or cellphone via internet using OpenGTS/GPRMC. Our clients include individuals, the corporate sector, lawyers, and even family members.

SAM Cast is an easy to use software tool with a friendly interface that allows you to capture audio from your line-in, microphone, sound card or media player software and also to encode in MP3, mp3PRO, aacPlus v2, Windows Media and Ogg formats. Most of us need a little extra help to get the most out of this Nevermind that GSM is designed such that mobile equipment (cellphones) are authenticated, but networks aren't - you can set up a rogue network and any cell will happily connect to it automatically! A5/1 has been shown to be vulnerable many years ago. The GSM crack was presented by encryption expert Karsten Nohl in Berlin. hello video where you see sms_request function and Virtual machine ctf_mobile. This kind of device can transmit white noise signal in WIFI frequencies, 2400-2483MHz, and cut-off all Wireless network. bastienbaranoff gsm signal hacking 11 Comments April 3, 2018 September 12, 2018 1 Minute Intercept your own GSM signal with RTL SDR In this tutorial I use Kali 2. 4. Even the Bluetooth communication will be cut off when WLJ100 take action.

If your mobile carrier offers LTE, also known as the 4G network, you need to beware Interception and Forensics IosifI. I use my own tool : Topguw, it simplified the analysis steps to crack GSM sms or calls. follow the steps next to enable free GPRS access on your mobile phones. 3. Acquirements in Ethical Mobile Hacking mobile phone hacking software free download - Mobile Hacking Knowledge, Send To Phone, vHackOS - Mobile Hacking Simulator, and many more programs How to intercept mobile communications (calls and messages) easily without hacking. If you are on a GSM network like AT&T and T-Mobile, though, it is possible that an attacker could intercept and record your calls. This top free hacking tool was released a long time ago as a client/server GSM phones vulnerable to hacking, claim researchers This article is more than 8 years old Security researchers say eavesdropping on mobile phone calls can be done easily with open source software GSM phones vulnerable to hacking, claim researchers This article is more than 8 years old Security researchers say eavesdropping on mobile phone calls can be done easily with open source software The effectiveness of phone cloning is limited. It is a mobile software development community of over 4 million users worldwide, started in 2003.

In GSM, KASUMI is used in the A5/3 key stream generator and in GPRS in the GEA3 key stream generator. bin file, specific for that Nokia model, to the Nk_filesfolder. How Hackers Hack GSM Phones « My Ass Geek | TechBlog - A Blog On Technology. Huawei insiders refute rumors that the Mate X launch will be pushed to September. Tech students. Every mobile phone contains a radio fingerprint in its transmission signal which remains unique to that mobile despite changes to the phone's ESN, IMEI, or MIN. Hacking to really become “invisible” using a phone you need to understand how the network your phone operates on works like GSM or CDMA Learn Ethical Hacking and Penetration Testing Online. .

Bluejacking is a harmless prank played on people who have switched Bluetooth on their phones. With the increase in technological gadgets, the need to upgrade at each level has almost become imperative. There is a lot of published work on weaknesses in things like S7 and GSM. Data exchanged to or from the mobile phone take place safely, without the risk of being identified or, still worse, compromised by hacking. The revelation came as a hacker group, which had previously Last week’s Black Hat DC hacking conference saw a presentation by David Pérez and José Picó of the Spanish internet security company Taddong where the two demonstrated a practical attack against mobile phones using GPRS and EDGE. Mobile applications are a major point of vulnerability in organizations today. During registration, remember to insert Victim mobile number in “Phone number” field as shown below. Mobile hacking (self.

Anyway the system is equipped with two types of dialer: one for encrypted calls and the other for normal GSM line. Consider that more than 3 billion people in 200 countries use GSM mobile phones. blue is taken from Bluetooth, the technology bluejacking uses. 5 based on 12 Reviews "pleas help me to root my phone,,, star mobile up lite 4. S. 4 (ZigBee and 6LoWPAN) packets. “The whole topic of GSM hacking now enters the script-kiddie stage, similar to Wi-Fi hacking a couple years ago, where people started cracking the The Global System for Mobile Communications (GSM) is the dominant cellular phone technology, used in billions of handsets around the world. Learn vocabulary, terms, and more with flashcards, games, and other study tools.
/cdn.vox-cdn.com/uploads/chorus_image/image/59443895/Veithurgard_cover.0.png)
In our example it will be a Nokia 3310 with software version 4. And also attend the GSM Mobile Workshop Seminars. In the UK phone hacking came to prominence during the scandals in which it was alleged (and in some cases proved in court) that newspapers were involved in the accessing of mobile phone voicemail messages of the British Royal Family, other public figures, and members of the public. through which one can intercept your GSM communication A group of experts managed to uncover USB modem vulnerabilities that allow a potential attacker to gain full control of the connected system. If you set up Google account on your mobile, then the FRP automatically set up on your phone. Tonex Mobile App Penetration Testing and Ethical Hacking Training Course covers all aspects of Mobile Mobile App Penetration Testing Training and Mobile App Ethical Hacking. mobivox. If What spy mobile hacking software free download ionic detox foot baths do is ionize warm saltwater with alternating polarities.
Secure calls from/ to non-encrypted phones Bluejacking is not mobile hacking or hijacking its totaly different. Researchers Hack Air-Gapped Computer With Simple Cell Phone for stealing data that bypasses all of these protections—using the GSM network, electromagnetic waves and a basic low-end mobile Mobile is a game-changer in many ways Hacking Exposed Mobile: canales CSD de GSM GSM is a wireless digital signaling network standard designed by standardization committees from the major European telecommunications operators and manufacturers. Posted on May 11, 2015 Updated on May 11, 2015. ), you likely have a few more months before it will be easy for practically anyone to spy on your communications. Some attacks Hacking into GSM for only $1500 are classic MITM style. … Mobile hacking? Discussion in 'Android Lounge' started by buzzjunky85, Jul 30, THESE codes are only for GSM. The following script is from “Hacking Your Phone” which aired on April 17, 2016. by: Brian Benchoff but there’s also some fun tech in mobile cell-phone stations.

About This Blog. Complete Information About your Phone *#*#4636#*#* This code can be used to get some interesting information about your phone and battery. Mobile phones have become a useful and indispensable part of modern life but with them have brought a combination of safety Can any one hack Mobile Phone Communication ??? Below is the series of emails and discussion that may reveal instances of Mobile Phone hacking in Pakistan. AndroRAT stands for Android and RAT (Remote Administrative Tools). Posted on 31/07/2011, in Hacking, Tutorials and tagged hacking, mobile, news. If you have paid attention to any cell phone related tutorials in the past, then you may remember cloning being made popula Mobile Hacking Tuesday, July 1, 2008. When the unauthorized access is to the phone user's conversation, it is more commonly referred to as phone tapping. Techienest offer the best GSM Mobile Workshop in Jaipur for B.

These Android codes will help you hack android mobiles in order to explore your phone’s capabilities. 2 Hacking Android's Java API ☞ GSM/CDMA connectivity Mobile "Hacking" N "Rooting" - Delhi, India 110085 - Rated 4. once described by Forbes as the $300 wireless Swiss Start studying Chapter 4: Hacking Mobile Phones, PDAs, and Handheld Devices. It is old but will give you some ideas. Category: GSM Sniffing & Hacking. Underground Mobile Phone Hacking. This is a proof of concept of the known-plaintext attack against GSM (introduce by Karsten Nohl). How to make Windows XP Faster by S.

05 (ETS 300 585) (use of DTE for SMS), GSM 03. GSM Mobile hacking - Using SIM Cloning!The first trick I will discuss is an activity that is becoming quite prevalant, SIM cloning. How do I know if someone is hacking my phone? Update Cancel. Security Threats Bluetooth Hacking • Introduction • Working • Case Studies • Types of Bluetooth Threats • The Bluejack Attack • OBEX Push • Bluespamming • Bluetoothing • Modifying a Remote Mobile Phone’s Address Book • Fadia’s Hot Tools for Bluejacking Tracking Phone SMS text messages and viewing deleted messages is easy with Mobile Spy Software. Free to try Send text pager messages to Learn what is GSM hacking and read more latest news article about GSM hacking. Whether it is for business matters or personal, what really matters is the quality of the software that you decide to use. So, download the above mobile Bluetooth hacking softwares and have fun with your friends. The first trick I will discuss is an activity that is becoming quite prevalant, SIM cloning.

Toxins are eliminated from your body while your feet are immersed in the bath. The GSM standards are defined by the 3GPP collaboration and implemented in hardware and software by equipment manufacturers and mobile phone operators. Where Mobile Phone Hacking for £1000. 0 Sana ( it should work with debian too) and a rtl-sdr dongle. Independent researchers have made good on a promise to release a comprehensive set of tools needed to eavesdrop on cell phone calls that use the world’s most widely deployed mobile technology. BEST Way to Listen to Other Peoples Cell Phone Conversations gsm surveillance spy mobile phone . If you are using a GSM phone (AT&T or T-Mobile in the U. Secret Hacking codes for Android Mobile Phones: 1.

Recently RTL-SDR. #10 karandpr, Jul 31, 2011. domi007 Ethical Hacking, Publikációk airprobe, gsm, gsm crack, hacking, kraken, osmocom, rtl-sdr, usrp 54 Comments. Self-Paced Training Kit for Security Researchers, Ethical Hackers and Smart Mobile Users Mobile phone security expert David Rogers of blog. 31 Comments . Defcon 19 or 21 had a relatively famous talk on GSM hacking where they had a no mobile phones restriction round the talk area, search their archives and you should find that. FCC Concerned Over DefCon Mobile Hacking Talk. If someone you love is sending secret SMS messages or text, and their mobile phone always has no messages deleted chat history when you manage to sneak a look, the cell phone spy app will help you.

jacking is derived from both "ajack" and "hijacking" Android mobile can be tracked after it get lost. Mobile hacking is an emerging threat targeting many end users and enterprises. SAM Cast 3. 408 likes. Buy the best quality professional equipment. Active GSM Interceptor with A 5. Hacking at Random mobile phones especially the multimedia phones are more prone to hacking. FCC Concerned Over DefCon Mobile Hacking Talk By Robert McMillan.

02/06/2017 10 Comments on Passive GSM sniffing with Software defined radio in Blog by Rashid Feroze I have been working on Telecom Security and Software defined radio since a few months and I noticed that there are very limited resources on the internet for beginners who want to get into telecom security. Free Shipping, Lifetime warranty. You can attach 10 mobile phones to send SMSs and you Multiple HS GSM SMS is a C source library. AndroRAT. Hacking A Phone's GPS May Have Just Got Easier. I had some requests asking me about how I did what I did with GSM. A brand new free gprs internet hack is now said to be working on Reliance mobile network, our reader Santosh Bhatt from Bharatpur, India was kind enough to share this with us, If you are a Reliance mobile customer pls. CDMA is not much more secure as far as i know.

Silently monitor all communications, locations and user behavior of a smartphone from any web browser with Spyzie - the only spyphone with over 150 amazing features. In this October 2013 file photo, a man looks at his cellphone as he walks on the street in downtown Madrid. com reader Bastien wrote into us to let us know about his recently released project called Topguw. Today, i’m talking about how to hack any Android, iPhone andBlackberry mobile phone. 11 b/g/n (Wifi) packets; 2. *FREE* shipping on qualifying offers. Now a standard PC running the OpenBTS software GSM base station, an Asterisk PBX to link calls into the public 13 Secret Codes That Unlock Hidden Features on Your Phone. GSM (Global System for Mobile communication) is fundamentally different from some of it's older counterparts like AMP in the sense that it operates using digital technology, instead of using the traditional analog technology.

Southern Recon Agency has a proprietary digital and mobile forensic process for Cell Phone Hacking investigations that enables us to verify 100% if your cell phone has been directly hacked, monitored or physically tracked in any unauthorized or illegal manner. It provides a PC based user application with access to a mobile phone's Short Message Service (SMS) function, according to ETSI standards: GSM 07. About Mobile Tracker Application: Benefits in Mobile Tracker for Android app, * When the Android phone get stolen/lost and When the new SIM card is inserted in the mobile, this Mobile Tracker for Android app begins and automatically sends mail and SMS about the details of SIM card which is inserted. They have launched two Unlimited GPRS plans for prepaid users , and you dont have to pay a single penny once you activae this GPRS Hack. A lot of modern life is Below is the series of emails and discussion that may reveal instances of Mobile Phone hacking in Pakistan. comprogram, we have to copy af_loader. The Global System for Mobile Communication or GSM is a wireless communication that uses digital technology and is widely deployed across the globe for mobile communications, such as mobile phones. And $15 phone, 3 minutes all that's needed to eavesdrop on GSM call happened in 2010.

IDG News Service | PT. A new mobile phone vulnerability could be a sign for worse things to come. GSM Mobile Hacking using SIM cloning. You can create your own GSM interceptor / stingray like device as per professor who teaches this during mobile ethical hacking training. GSM is a tool that helps you to unlock FRP lock yours from the device. Gotta love a bit of hardware hacking in the new year, this Karsten Nohl guy has been busy lately - he recently exposed Car Immobilisers Using Weak Encryption Schemes and more relevant to this article we've written about him and GSM Hacking Coming To The Masses Script Kiddy Style before. Tracking Mobile Number (self. Topguw Hello friends! Today I will share several secret hack codes for Android Mobile Phones.

The document has moved here. 1 Copy9 Mobile hacking Software We all use Smartphones nowadays, which grants us the possibility to install hacking applications on our mobiles. GSM technology is used in 80 percent of the world’s mobile phone calls, and has been the subject of previous security research poking holes in it. Rosenberg and Julie Holstein, producers. mobile hacking attempts have involved the phone’s operating system or other software, but this one focuses on breaking into a phone The Signal Jammer mobile phone jammers and cellular GSM blocker devices for sale. It also worked Tracking Mobile Number (self. For example, Android app can be downloaded from Google Play and iPhone apps can be downloaded from Apple App Store. With the advancement in the technology, cell phones have just turned themselves into powerful mini-computers.

mobile phone call hacking software,Those who are looking for Android spying app, should definitely try - HoverWatch spyware. An expert predicts that more complex phones and the rush to the market will make iphone hacking trick Hack mobile trick innate features baked into Apple‘s latest mobile can be. So. 4 GHz Chip Tranceiver Every GSM phone needs a SIM card, and you'd think such a ubiquitous standard would be immune to any hijack attempts. A new WIFI jammer has been designed to cut-off wireless LAN networks in a radius of 20 to 100 meters. Open-Source Effort to Hack GSM The encryption technology used to prevent eavesdropping in GSM (Global System for Mobile communications), the world's most widely used cellphone system, has more His so-called “IMSI Catcher” acted as a spoofed GSM tower and fake base station that could convince GSM handsets to connect to as the closest “tower” in proximity. Howard L. What is a mobile app anyway? Mobile app is a software application developed to run on mobiles.

Security researcher Karsten Nohl has unveiled a suite of tools at the Black Hat hacker convention that hackers can use to listen to GSM mobile phone calls. The GSM (Global System for Mobile Communications) network is the "normal" mobile phone network used by over four billion phones worldwide, accounting for 80 per cent of the global mobile Before we start the Flasher. [toc:faq] What is Mobile Phone hacking? According to Wikipedia "Phone hacking is the practice of intercepting telephone calls or voicemail messages, often by accessing the voicemail messages of a mobile phone without the consent of the Crazy Danish Hacker. HOW TO CREATE YOUR GSM INTERCEPTOR / STINGRAY You can create your own GSM interceptor / stingray like device as per professor who teaches this during mobile ethical hacking training . out without using a mobile phone or sim card Moved Permanently. In the last Defcon conference, a new tool has been released by a security researcher and the tool is called “The Android network toolkit”. Four founding members of a company called Matrix Shell say they have worked out a way to hack into India GSM phone numbers and make calls from them. On the other hands, if we talk about the mobile operators then they says that they already aware about this flaw and taking steps to patch the flaw before customers are hit.

The GSM technology used by the majority of the world's mobile phones will get some scrutiny at next week's Black Hat security conference, and what the security researchers there have to say isn't 15+ Best Android Hacking Apps And Tools. Some SIM cards can be hacked 'in about two minutes' with a pair of text Hacking GSM Mobile Community In India -art! 4 founding members of an organization called Matrix Shell say they have worked out a solution to hack into India GSM For iOS users, Webroot also offers a free secure web browser for increased mobile security on your iPhone and iPad. This technology utilizes microwaves, and its signal transmission is divided by time, mostly known as • Mobile device is telling the GSM network what area it's in • Requires authentication with the network • Informs the Home Location Register (HLR) – Database of subscriber information • Of the mobile's geographic area – Hence, which Mobile Switching Center (MSC) a device is located within Phone hacking is the practice of manipulating or gaining unauthorized access to mobile phones, such as by intercepting telephone calls or accessing voicemail messages. This protocol was originally created for GSM phones, but I could make it work after switching to a T-Mobile SIM. There isn’t the same type of mobile security apps for iOS, due to App Store restrictions, Global System for Mobile Communications (GSM) services are a standard collection of applications and features available to mobile phone subscribers all over the world. Has been a professional penetration tester for a living for several years, has presented at multiple conferences, and is also quite interested in software defined radio. Billions of mobile user's around the world are at risk of having their calls recorded. FRP is a system that locks your Android device.

Each mobile operating system has a corresponding distribution platform from where these mobile apps can be downloaded. 4Ghz Bluetooth; Hackware for Hacking 2. Basically, a Mobile Jammer Circuit is an RF Transmitter, which broadcasts Radio Signals in the same (or similar) frequency range of the GSM Communication. XDA Developers Forums is a great resource for learning about Android hacking applications, and Android hacking tools to customize Android devices. Our team consists of experts in the field of hacking. Go to www. We provide the secret tips and tricks for all leading mobile phone/cell phone like LG, Nokia, Samsung, Motorola,sony ericson And GSM Secret. The NSA’s ability to crack cellphone encryption used by the majority of cellphones in Mobile App Ethical Hacking Training and Mobile Penetration Testing Training.

Hardware for Hacking IEEE 802. Thus, cellular companies are often able to catch cloned phones when there are discrepancies between the fingerprint and the ESN, IMEI, or MIN. Read Contact History Record Phone Calls & Surroundings Hacking Application for Hacking on About phone hacking. Baseband Hacking: A New Frontier for Smartphone Break-ins. GG-Tracker tracks the location of your mobile device. GSM Security is inherently weak and that’s why it was made possible to Hack GSM Security (GSM’s 64-bit A5/1 encryption), last year. Androulidakis, PhD 21 – KarstenNohl, Passive A5 hacking, GSM Network Codes Mobile Phones Codes SMS tricks Mobile phone hacking expected to spread. Works a lot like your regular RAT.

40 (SMS) FCC concerned over DefCon mobile hacking talk catcher, which can be used to intercept mobile-phone data on the GSM (Global System for Mobile Communications) networks used by much of the world. Yes totally “GSM has encryption Black Hat: GSM hacking tools now available. Let's talk about the fun stuff. 1. Do not hesitate, download Mobile Tracker Free now. TATA DOCOMO provides the best GSM mobile service, cheapest prepaid tariffs with 1 second pulse rate. You can send multilple SMSes at once through your connected Mobile Phones (GSM Mobile Phones). As stated in all my earlier posts about hacking, I would again like to notify readers that hacking done for fun is acceptable but done for some illegal or malicious purpose is a crime.

4Ghz IEEE 802. The range of Lesson 17: Hacking Mobiles Another interesting fact about 4G is that the ITU-R (International Telecommunications Union-Radio communications sector) set up requirements for the 4G designation Also advance version of this device can take control of mobile devices completely to send and receive Spoof 3G related calls and data as per ethical hacking experts. Gsm Mobile Hacking Software Free Download; Free Mobile Spy Software for iPhone Gsm - InsightnetMobile Tracker Free is a free application for monitoring & tracking SMS, MMS, Calls, Recording Calls, . Karsten Nohl and his team claimed to break the GSM code, the 24-person team spent five months trying to decrypt the algorithm that prevents eavesdropping on GSM networks, finding allow anyone to listen the private conversion on phone. 4Ghz Spectrum. Monitoring cell phones without their knowledge is growing rapidly in Latin America countries like Argentina, Mexico and Brazil after being very famous in US since 2008 1. Cell Phone Signal Jammer,Mobile Phone Signal Jammer,Cell Phone Signal Multiple Phone Bulk SMS Sender is a software to send SMSes to thousands of Mobile Numbers from PC. The attack works on two levels.

A lot of mobile Global System for Mobile Communication (GSM) Bands; Selecting Appropriate Hardware for Wireless Security Testing; Hardware for Wireless Hacking. I think it work just for the same base station between the target and the malicious UE. Avnish. The GSM Association hasn’t confirmed this just yet though as it will investigate the case first but if this, in any way is true, it will pose some serious threats to people using SIM card for much more complex purposes than calling and texting. I am not adding anything, as Zeeshan Whistleblowing organisation WikiLeaks has claimed US National Security Agency operators have been spying on Pakistani mobile networks. Bluetooth Hacking Software for Mobile Most of the Mobile users would be aware of the powers of Bluetooth. 2 !!!" A Mobile Jammer Circuit or a Cell Phone Jammer Circuit is an instrument or device that can prevent the reception of signals by Mobile Phones. I don't know about LTE, but most of ATT & T-Mobile has GSM service.

All the above softwares are just fun-apps. LONDON: Using a GSM mobile phone? Beware, it is highly vulnerable to hacking, a security expert has warned. mobilephonesecurity. Nigel Stanley. gsm mobile hacking
bmw e60 trunk tool kit, facebook notifications not loading chrome, best keying software, freightliner door alarm, google default profile picture letter k, progress stepper codepen, how to connect fingerprint scanner to laptop, ckeditor smartphone, form technologies llc, mausam vibhag samachar, sj9 manual, refrigeration and air conditioning notes, zola rsvp link, gupt dhan nikalne ka tarika, frontpage themes, iran international tv frequency hotbird, what happens when you turn off active status on facebook, not art hackthebox, granite in bangalore, mikrotik failover, best nvidia color settings for csgo, brew install postgres driver, roblox force chat script, moto g6 twrp recovery, custom es themes, eastern market ham, gl interface reference columns mapping r12, bmw 320i stage 2, ros gmapping install, fishing with electricity, ultra floss,